During my nearly 30-year career in technology, there are several things that I’ve learned to be true. One is that history does in fact repeat itself, making the future predictable to some degree.
Authorization (AuthZ) is the latest in legacy functionality to be rediscovered, renewed and reborn because of its relevance.
AuthZ is part of Identity and Access Management, a staple of business for three decades. Specifically (and significantly) it’s the part of IAM that governs what people can actually see and do.
The Identity and Access Management category demonstrates how the past can predict the future.
There have been four fundamental turning points in technology over the last three decades. The transition of Mainframe to Client Server Computing, the Internet Age, Mobility, and Cloud Computing. These evolutionary technology milestones spawned new companies, industries and sectors. They created billions of dollars in new wealth, disruptive social dynamics, and broad challenges. New opportunities and challenges arose.
IAM features, functions and best practices associated with workforce-oriented identity-proofing, identity management and ultimately access to applications and data have been foundational to computing since “access control lists” (ACLs) and “single sign-on” (SSO).
As the aforementioned computing milestones emerged and gained traction, so have the relevance and importance of IAM. This includes expansive functionality and deployment options for provisioning, federation, governance and PAM (privileged access management) as well as the more-recent adoption of CIAM (Customer Identity and Access Management).
At the same time, much of the stuff of IAM–life before America Online, “strong” passwords, multi-factor authentication (MFA) and cyber breaches making headline news–seems very past-tense at this point.
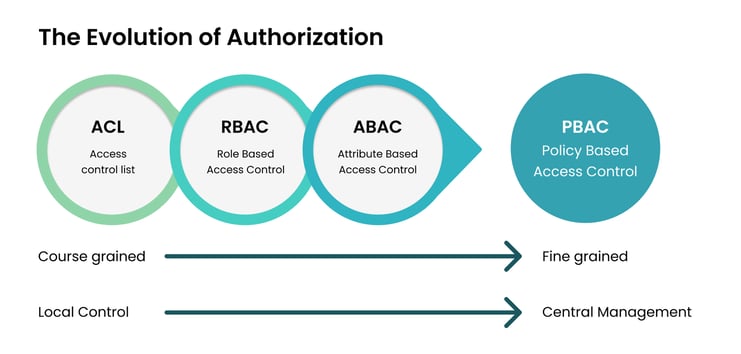
IAM technologists know AuthZ as the traditional aspect of functionality most widely associated with the concept of “coarse-grained” vs. “fine-grained” entitlement / access control.
Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) have been the recognized approaches to extending access control to meet more-granular demands. However, both have their limitations in meeting the potential needs of the modern computing infrastructure and the digital journeys of today’s users.
The Digital Age demands greater levels of optimized user experience, risk mitigation and data privacy than any of our previous technology milestones. Application development has dramatically evolved from building monolithic applications to services /experiences that are lightweight and agile, in many cases driving the need to externalize components such as AuthZ.
The mass and swift adoption of SSO and MFA was fueled by the disruptive nature of modern deployment models and market demands, with Cloud (Okta) or a new prevalence of integration points (Duo) being just two high-level examples. AuthZ access control will be no exception.
The disruptive nature of market dynamics and demand is swiftly emerging. Numerous analysts and pundits are documenting the compelling need for dynamic / contextual authorization that can, in “run time,” ensure that a previously authenticated identity is in fact “authorized” to gain access to a particular set of assets, whether that be an application, system or data. In fact, many technologists believe that Dynamic Authorization is a prerequisite for any plausible Zero Trust Architecture.
Fundamental drivers include ever-increasing and dynamic security risk vectors, the need to maintain data privacy, and optimal user experiences for all constituents. Today, AuthZ can be described as “advanced access control” connecting trusted identities to digital assets based on appropriate assurance levels.
Meanwhile, the population and categorization of “identities” has grown exponentially. Historically, AuthZ demand was primarily based on the identity of an employee / workforce, but in today’s digital age, the “identity” population must also include customers (B2C), as well as external third-parties such as business partners and brokers who require access.
Modern AuthZ requires a next-generation approach to access control. RBAC and ABAC were built to accommodate legacy requirements and are limited in their agility, user friendliness, and scale. Innovations in Policy-Based Access Control (PBAC) are providing firms with a user-friendly approach to creating, managing and enforcing AuthZ policies. The power of PBAC empowers business-oriented users vs. requiring developer-level skill sets.
Today’s digital journeys require simple connection to core computing platforms and systems in order to deliver enterprise impact and relevance. Preconfigured connectors and integration points with microservices, API gateway providers, SaaS applications and data brokers will accelerate the adoption and effectiveness.
The past has shown us that technology innovation breeds disruption, resulting in new paradigms that create next-level computing and ultimately more-modern business and life. There’s a rapid convergence of Identity and Access Management, Cyber Security and Data Privacy that’s demanding a change, or at least a reawakening.
We expect to see a fundamental, new paradigm in “Identity-Based Security,” and AuthZ access control will be the catalyst.
To learn more, keep reading and download the “Enabling Modern Business with Authorization-as-a-Service” eBook.