What is Policy as Code?
Policy as Code is the use of code to represent policy – rules and conditions for access policies that determine when access is authorized. Policy as Code enables development teams to manage and automate policies by integrating policy workflows into existing CI/CD pipeline and test processes more efficiently. Simultaneously, security teams can have greater visibility and control of access policies and their deployment when it’s done within a centralized management platform.
The Policy as Code approach is a growing practice in code development to manage all aspects of authorization as part of the application lifecycle. Infrastructure-as-code is an established method for managing repeatable and versioned application deployment. Similarly, Policy as Code extends this approach to the realm of authorization and the access policies that enforce it.
Why is Policy as Code needed?
While Policy as Code has immediate impacts to the CI/CD pipeline, its best practices have multiple impacts on the business:
Improved collaboration: Multiple stakeholders can contribute and review policies in a centralized – facilitating collaboration between security, compliance, business, and development teams.
Enhanced visibility: Policy as Code makes it easier to track changes, identify authors of those changes, and trace the evolution of the policies over time through version control – providing visibility into changes and ownership.
Accelerated time-to-market: Enterprises reduce human errors that occur when policies are manually managed. Automated processes for verifying and testing policies improve the efficiency and security of the policy rollout.
Ease of auditing and compliance: Policy as Code (when used with an authorization platform) simplifies auditing and compliance to support standards such as GDPR, HIPAA, and PCI-DSS.
Policy as Code adds to the benefits of existing developer-friendly approaches at an enterprise. However, when used as part of PlainID’s Authorization Platform, stakeholders responsible for policy management gain even greater visibility and control of user access to best manage, update, and tweak policies towards user adoption and security compliance.
Policy as Code with PlainID
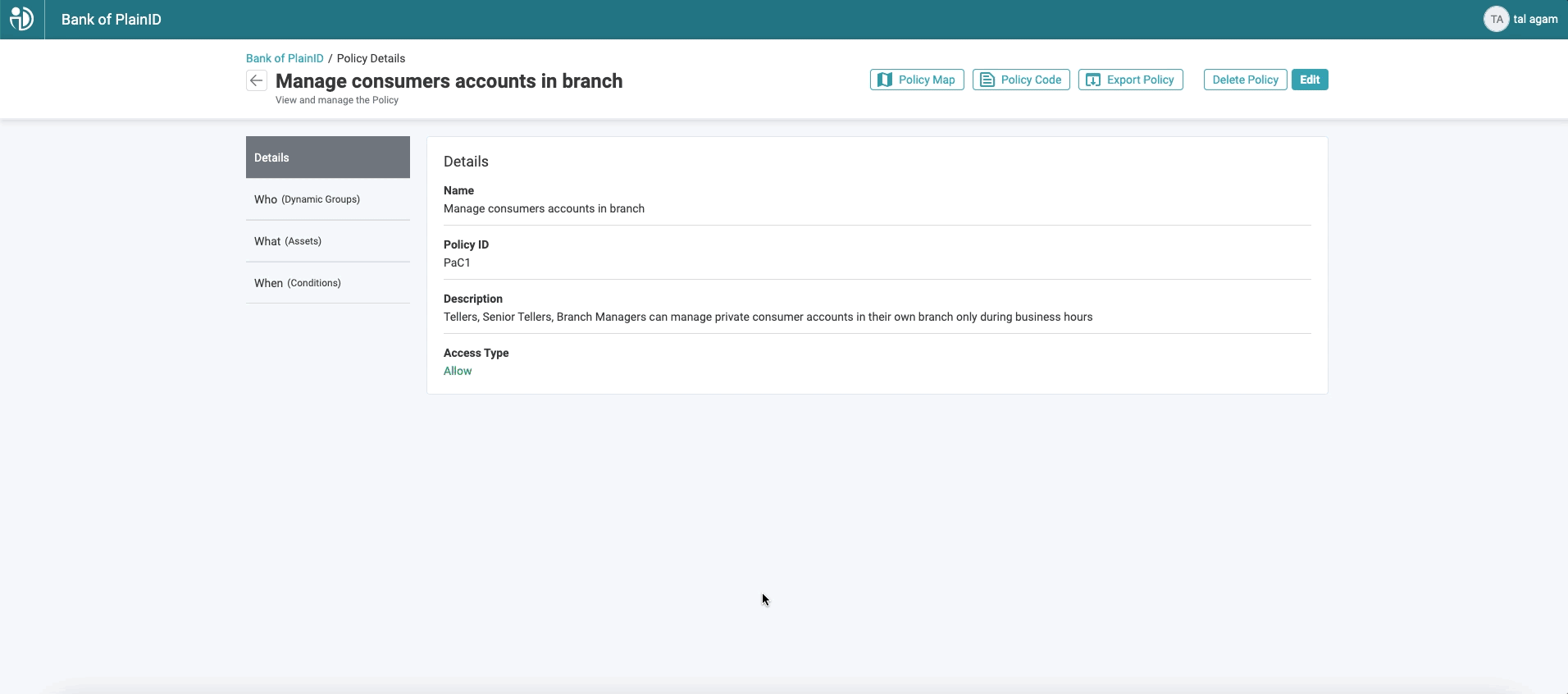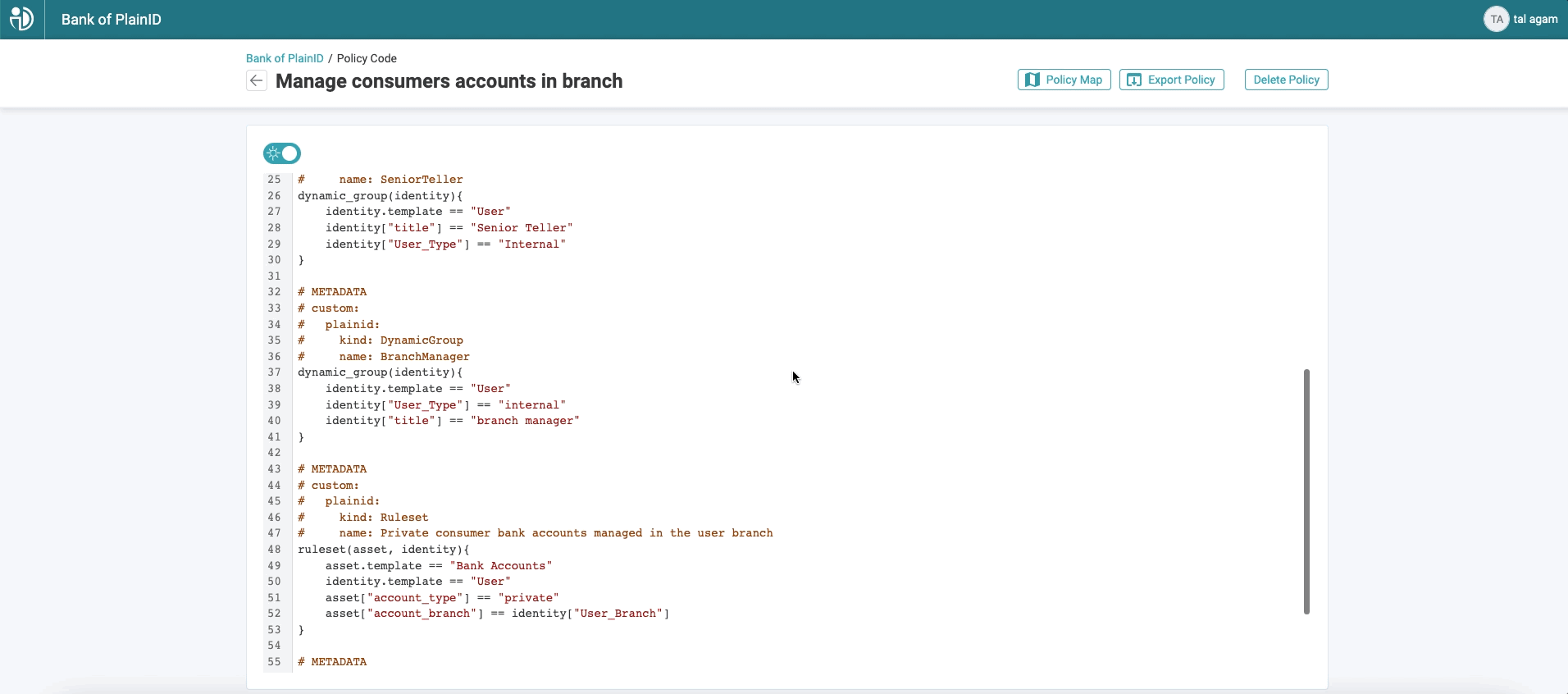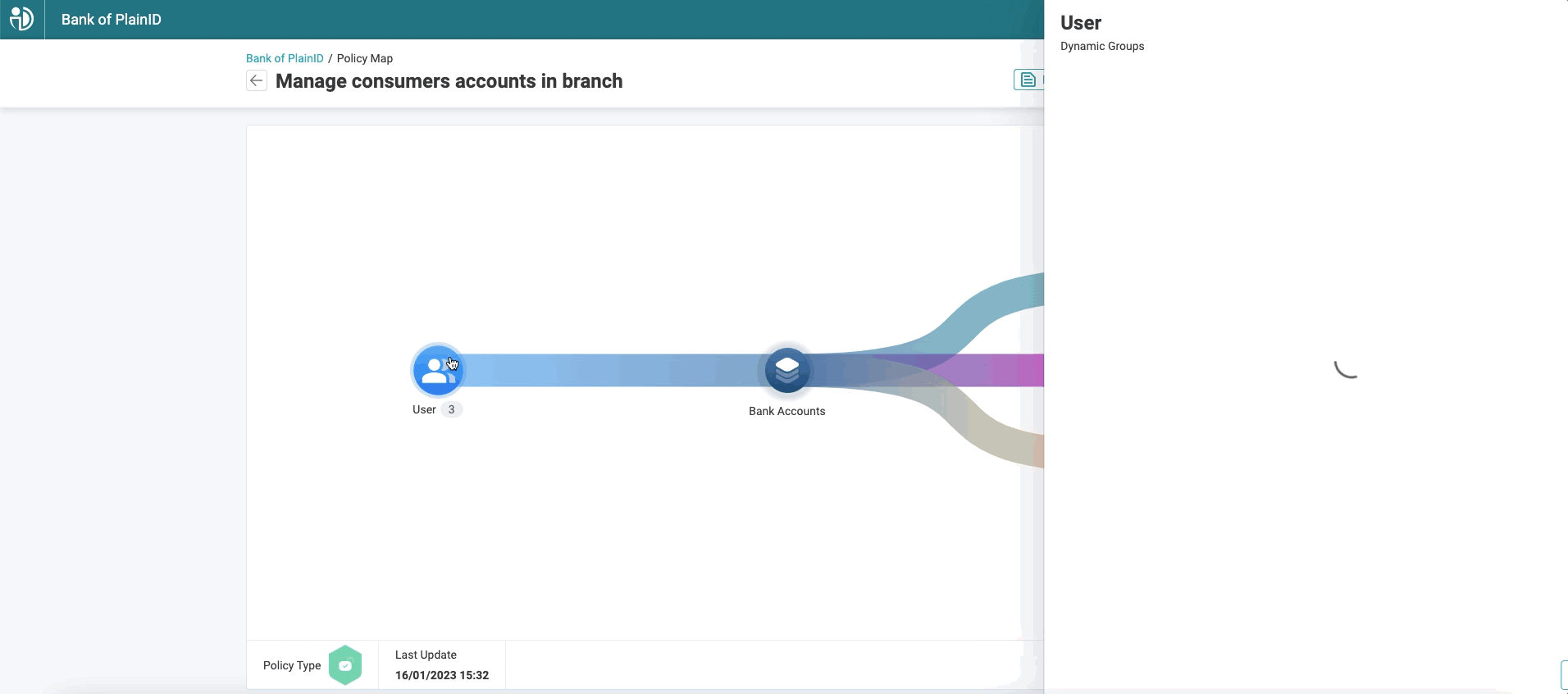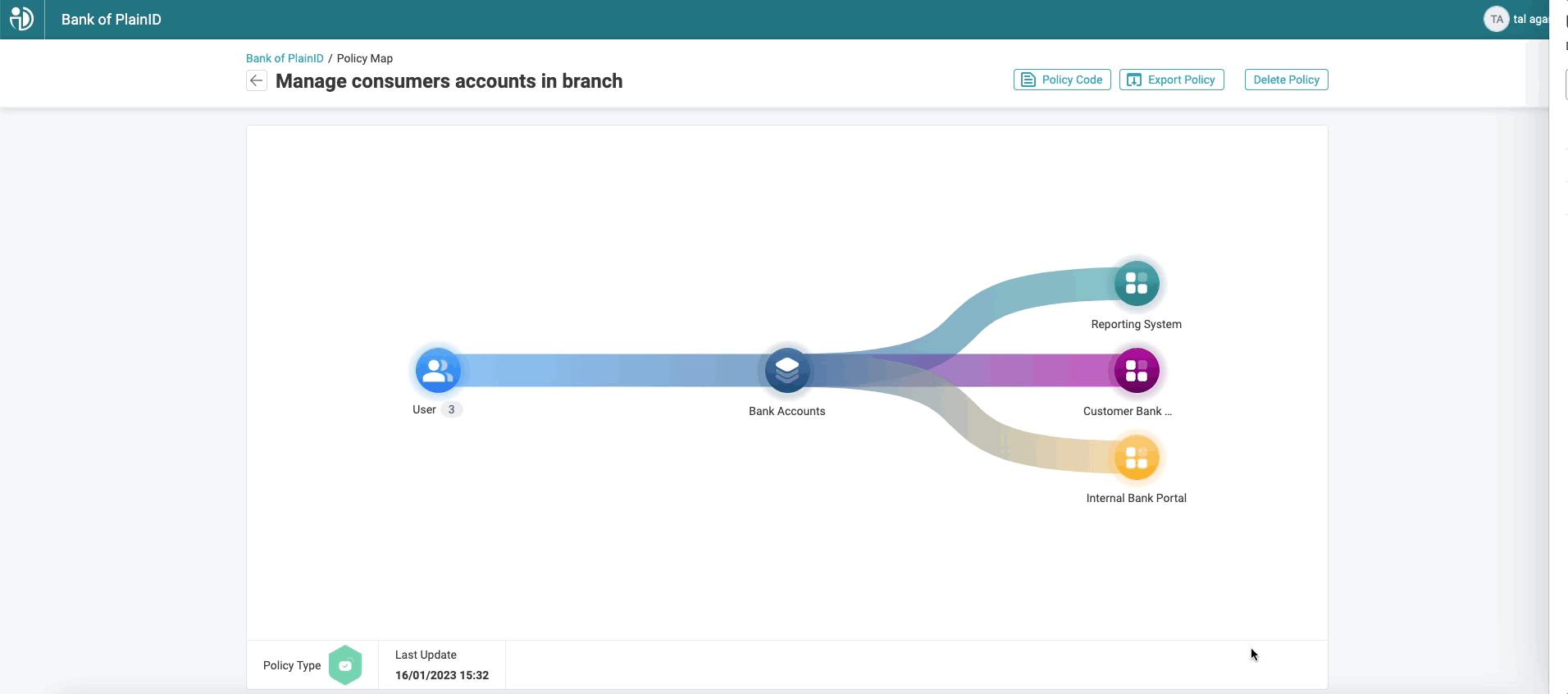
As most developers use REGO-based policies with tools such as Open Policy Agent (OPA), PlainID standardizing on REGO supports the wider developer community and helps enhance adoption. PlainID policies can be translated to REGO, and policies written in REGO can be used by the PlainID Authorization Platform. PlainID continues to build capabilities on this foundation providing flexibility and support to developers and application teams who already enjoy Policy as Code features.
Policies consist of Dynamic Groups, Rulesets, and Conditions that represent the "who can access what, and when" structure. With PlainID’s standard for annotating REGO objects, any REGO-based policy that is formatted accordingly can be ingested by the PlainID Authorization Platform. These metadata annotations connect PlainID’s policy building blocks to REGO code blocks giving customers the best of both worlds: Policy as Code for developers; and visible, readable representation for business and security teams.
This approach makes it easier for developers to apply pre-defined policies to their projects without leaving their existing tools, while also giving business and security stakeholders the ability to view, understand, and test policies – ensuring the needs of the business and the requirements of security are both met. For example, when a developer edits a policy, a business or application owner can easily visualize the flow within the Policy Mapping tool of the platform and investigate/test the policies without ever leaving the PlainID UI.
Using Policy as Code within PlainID’s Authorization Platform provides greater control, visibility, consistency, and standardization of access control across applications, APIs, microservices and data. Furthermore, a standardized approach towards policy management and rollout accelerates time-to-market that does not compromise on security.
For more information on Policy as Code, visit our documentation here:
https://developer.plainid.io/docs/policy-management/polman-policy-management